The internet is full of trackers, hackers, and snoopers. Every click, search, and download can be monitored. Proxies help you stay anonymous. Proxies act as a middleman, masking your real IP address. This makes it harder for anyone to track you. But how effective are they? And how do they compare to other privacy tools? Let’s break it down.
What Are Proxies and How Do They Work?
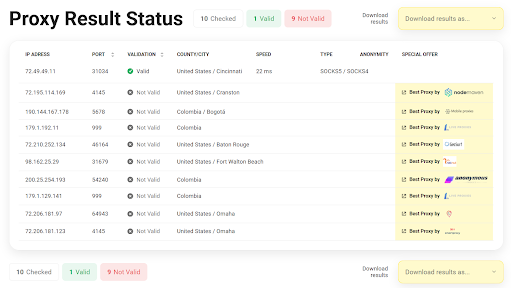
To connect online users rely on proxies, which function as intermediaries between their network and the internet. Your internet requests pass through the proxy server before reaching their destination website. When you send a request through the proxy server, your genuine IP address remains hidden from view.
During website visits, your proxy reveals its IP rather than your original one. A proxy generates an additional barrier that prevents website advertisers and hackers from discovering user activities and their sources. Proxy servers store website data from popular pages to minimize page loading times when users revisit the sites.
The Role of Proxies in Online Anonymity
Proxies serve as vital instruments that maintain privacy for your internet activities. Proxies serve two functions to protect you by concealing your IP address while simultaneously providing various resources for tracking prevention. The following functions allow proxies to support your anonymous behavior:
- Your IP address becomes hidden through proxy services to stop website advertisers and hackers from tracking you. Through proxy service, your original IP address becomes invisible while the proxy utilizes its own address to prevent activity tracking.
- Proxy servers offer users a way to pretend they exist in different locations which enables them to access content controlled by geographical restrictions. These features are essential for people traveling abroad and expats, as well as those living under censorship laws.

- Targeted advertising and profiling operations occur when users avoid being tracked by data brokers and advertisers. Profiling activity becomes more challenging through proxies because they redirect traffic from its original source.
- People face elevated security threats when using public Wi-Fi networks. Data interception occurs alongside fake website redirection from hackers when using public networks. Access to security benefits from a proxy IP obscurity yet a VPN grants complete security protection.
- The practice of Internet service providers (ISPs) to monitor browsing activities and sell collected data exists. Your proxy service maintains site privacy through its protection methods. The security of most proxy connections remains incomplete because they fail to provide traffic encryption. Hence, sensitive operations such as banking require additional defense mechanisms.
Types of Proxies for Online Privacy
Different proxy types exist with their individual characteristics.
- Forward Proxies: Forward Proxies accept user requests to forward them toward a destination server. Business organizations implement proxies to inspect data content and regulate network accessibility.
- Reverse Proxies: The reverse proxy stands ahead of web servers to control traffic entering the server infrastructure. The proxies manage server workloads while providing security capabilities.
- Transparent Proxies: Users normally remain unaware of proxy services because they operate underneath their awareness. Businesses alongside public Wi-Fi providers implement these proxies to perform monitoring and filtering tasks.
- Anonymous Proxies: Anonymous Proxies conceal your IP address but disclose the usage of proxy services to the destination server. You can utilize this proxy to escape restrictions with the downside of revealing some details about your operation.
- Elite Proxies: The elite proxy known as high-anonymity provides both IP address protection and masks the usage of a proxy server from discovery.
- Residential Proxies: Residential proxies operate from actual internet service provider IP addresses, which improves their capacity to evade detection and blocking processes.

- Datacenter Proxies: The speed of datacenter proxies makes them easier to detect since they originate from data center locations.
Proxies vs. Other Privacy Tools: How Do They Compare?
Multiple privacy tools exist beyond proxies. The purpose of proxies remains clear, but users wonder how these tools compare with privacy solutions, including VPNs, Tor, and other available options.
- Proxies vs. VPNs: Proxies by travchisproxies.com give IP address anonymity, whereas VPNs provide both IP privacy and complete traffic encryption protection. Security benefits derive from VPN technology because it adds protection to all data transmission. These proxies deliver quicker speeds and function better than other solutions when trying to access region-blocked material.
- Proxies vs. Tor: Through its multilevel server system, Tor provides users with the highest level of confidential traffic routing. You will achieve better security with a proxy, but it provides slower performance. Your network speed benefits from using proxies, while the Tor system delivers the most secure anonymity features.
- Proxies vs. Private Browsing Modes: Incognito mode stops local history storage yet fails to keep your IP address hidden. Network proxies supply true anonymity to users through their service.
Each tool has trade-offs. Quick anonymity can be achieved effectively through proxies because they operate as lightweight systems. VPNs provide better encryption. Tor offers maximum privacy protection, although it provides slow performance. Using several tools simultaneously represents the most effective method for achieving optimal security.
Conclusion
Proxies offer a straightforward way to increase online privacy. They hide your IP, bypass restrictions, and provide some level of anonymity. But they aren’t foolproof. Not all proxies offer strong security. And they don’t encrypt data like VPNs.
For full privacy, use multiple tools. Combine proxies with VPNs or Tor for better protection. Be cautious with free proxies, as they may log your data. Online privacy is a moving target. Staying informed and using the right tools make all the difference.